No, you should not make your passwords complex and super long! This will only lead to you forgetting the password and then later reset to one that you will actually remember – which, of course, we know will be super dumb and easy to crack.
Instead, you should go for passphrases. These are basically passwords, but longer and easier to remember. For example, a passphrase can be:
pancake lord on moon vacation three times left turn
According to Security.org’s password check, this would take a computer of today’s capacity about 1 unvigintillion years to crack. How many years is one unvigintillion? I don’t know, but I do know that I definitely won’t be around by then.
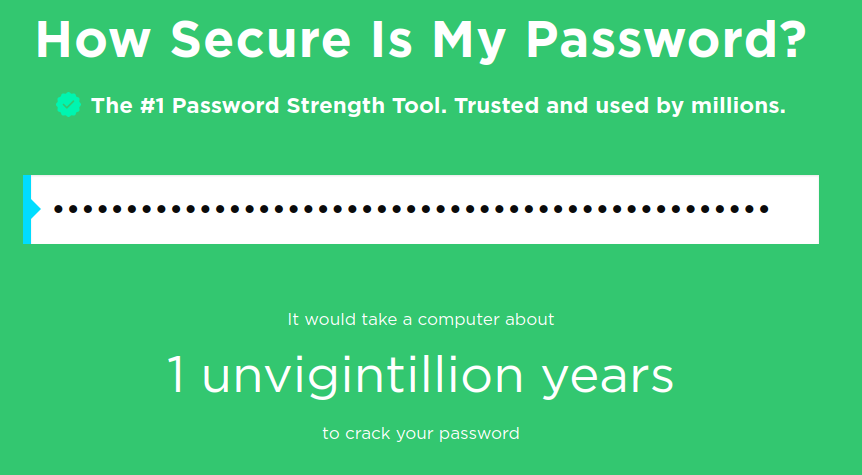
The reason for it being hard to crack this passphrase, isn’t the complexity, but rather its length. The longer the passphrase, the more possible combinations any brute force attempt needs to perform.
But, you ask, what about the required password complexity of sites, operating systems and the like? The lowercases and uppercases, special characters and such?
Well, that’s where password managers come into the picture! You see, there’s a lot of password managers out there and chances are you’re using a web browser with one built-in, right now! There are even services that let you store and access your passwords in the cloud for convenience, for example when you’ve lost access to your computer or device.
With a password manager, you can generate a super random and hard to remember password that fulfills any uptight requirements of an account registration. The point is that you will never need to remember it, the manager will!
The problem with most built-in managers though, is that they are exposed to the internet, meaning that if the client or browser is compromised – so are your passwords. The same goes for any online service that promises security – it’s all fine and dandy and cherries until the service is hacked and your passwords are stolen. This happened a while back with LastPass where, even though encrypted, users’ vaults were stolen and could potentially be cracked. This is exactly why centralization is bad – it gives hackers a single point of entry for thousands if not millions of users.
Now, how to avoid this? Well, firstly you should avoid centralization. But you cannot avoid hackers on the internet unless you go offline, of course. It might sound like a bummer, but that’s why I’m writing this post, you see!
Here’s where KeePassXC comes in. KeePassXC is an excellent password manager and vault that is secure, open source and totally free. KeePassXC is an application only, meaning no servers to connect to – all it needs is the database to keep its records. Already here, we’ve eliminated one potential threat in that we’re not exposing our passwords to the intertubes. The database can be safely stored where ever you like, for example in your home folder or on an encrypted drive. You can have multiple databases, for example one for private passwords and another for work related passwords (which I would recommend.)
So it’s easy to get started, just download and install the application. For Ubuntu/Debian users, I strongly recommend to install the PPA and use APT to install, instead of snap.
After installing and running it for the first time, you can create a new database. Set a passphrase, one that you can actually remember, because if you forget it you lose access to the database. I also recommend that you create an encryption key which can preferably be stored onto a physical drive for added security.
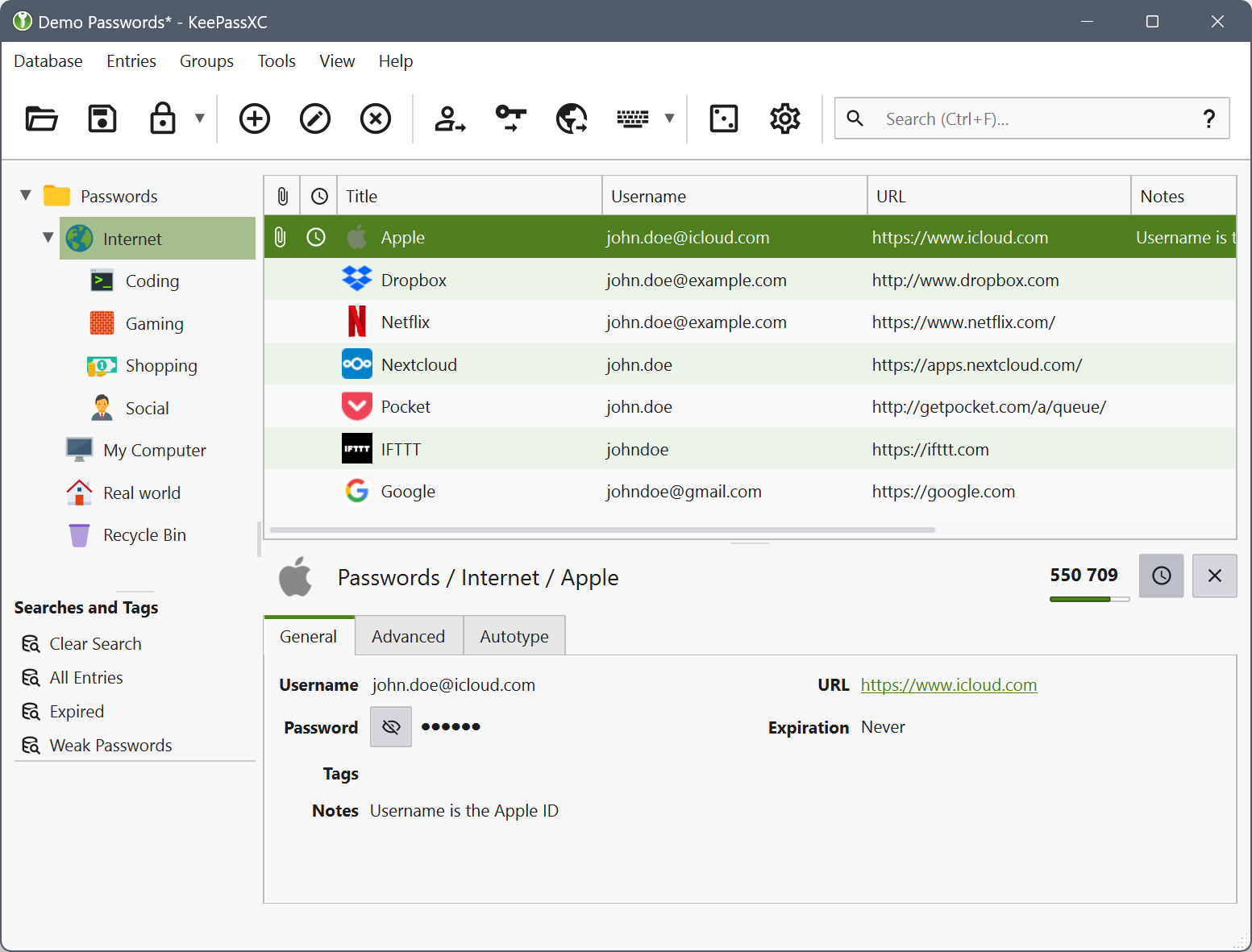
Once the database is up and running, all you have to do is store all your passwords. As you can see in the above screenshot, you can even use it for two-factor authentication. You can associate the entries to their respective sites and applications, organize them in groups and add icons to the entries.
I would however recommend that you install a browser extension, otherwise you would need to go back to the application every time you need to log onto a site. There’s an official extension for the most popular browsers, called KeePassXC-Browser. Once installed and configured (and the main application running in the background) it will ask for database password and fetch the associated entry when autofilling the login forms on a site.
A word of warning though: It’s known not to work with snap installations of browsers, which is the default installation method in Ubuntu. Be sure to use the APT version of both the web browser and KeePassXC and you should be good to go. Oh, you might have to add a permission entry in AppArmor if you’re getting “Cannot connect to database” errors, though.
Also, you might want to have some sort of cross-device sync. I know, this contradicts what I mentioned earlier with having the database offline, but the alternative would be manually copy over database and encryption key to every device each time you’ve added or updated an entry. Not too convenient. As long as you don’t use a centralized service, I believe you’re good though. For example, using a Nextcloud instance, you can sync between selected devices. As for mobile applications, for Android, there’s KeePassDX that’s fully compatible and also can use Nextcloud mounted storage to access the database. This is the one I’m using and can recommend.
All in all, I’m really satisfied with KeePassXC knowing that I’m in total control over my password vault and that I’m one step further from allowing Big Tech to have control over my online life.
